User Manual
91379030
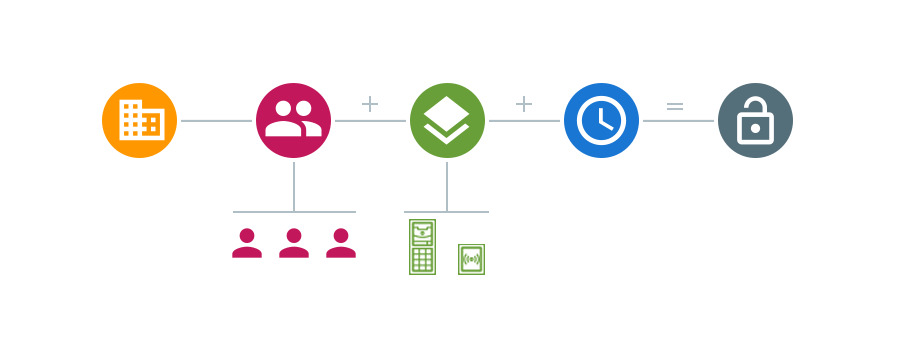
Abstract
Firmware 3.0
Manuals for previous firmware versions can be found at https://wiki.2n.com/acc.
Table of Contents
- Symbols and Terms Used
- General Information
- Installation
- Basic Access to Interface
- Logs
- Companies
- Users
- Groups
- Zones
- Devices
- Access Rules
- Time Profiles
- Attendance
- Visitors
- Presence
- Reports
- Area Restrictions
- System Setup
- Troubleshooting
- Supplementary Information
Can we advise you on anything else?
Take advantage of our technical support and sales specialists.